Why you’ll be able to belief TechRadar
We spend hours testing each services or products we overview, so that you will be positive you’re shopping for the perfect. Find out more about how we test.
Threatlocker was based in 2017, so we will say it stepped into the cybersecurity ring solely lately. Whereas expertise is definitely useful on this trade, there are strengths in ‘new blood’ that can’t be ignored. On this overview, we’ll take a better have a look at its endpoint protection safety platform, and see the way it fares in comparison with Kaspersky, Symantec, and different heavy-hitters.
Threatlocker: Plans and pricing
Sadly, Threatlocker doesn’t checklist the pricing for its endpoint safety platform on the web site. As an alternative, potential prospects are invited to contact the corporate’s gross sales division by way of electronic mail, or telephone. The excellent news is that reserving a product demo with one of many firm’s ‘Cyber Heroes’ is comparatively simple, and there’s a 30-day free trial that doesn’t require cost information.
Threatlocker: Options
In our “finest endpoint safety” collection, we’ve reviewed virtually all platforms value a dime and we will let you know immediately – Threatlocker’s array of options is nothing wanting spectacular.
Its primary product web page does an awesome job offering an summary of various options, in addition to displaying among the extra primary ones reminiscent of app black and whitelisting. What actually caught our eye, although, is the ‘Ringfencing’ function, which lets you set boundaries for a way apps work together with one another.
Sadly, there isn’t any devoted firewall for shoppers, but it surely does have one thing referred to as ‘Dynamic Community Management’. This can be a function that permits IT groups to manage visitors, or open ports for licensed apps solely. It makes use of dynamic Entry Management Lists (ACL), or agent authentications.
In accordance with Threatlocker, it is a safety hole that’s typically missed in endpoint safety platforms, and that may typically spell catastrophe if a malicious system infiltrates the community. Rightly so!
The platform’s coverage engine can be fairly superior, and can be utilized as a firewall, to limit what apps can do. Threatlocker refers to ‘Allowlisting’ as a technique to management the software program, scripts, executables, and libraries working on the endpoints and servers. The ‘Permit Checklist’ will be unique, too, blocking any apps that aren’t on it.
There may be additionally an choice to set time-based insurance policies, permitting apps to carry out sure capabilities solely at a pre-set time of day.
Threatlocker claims buyer assist is all the time accessible, both by way of telephone or the primary portal. It additionally says it “strives” to reply each name inside 30 seconds, and resolve each subject “on the identical name”, inside minutes.
Threatlocker: Setup
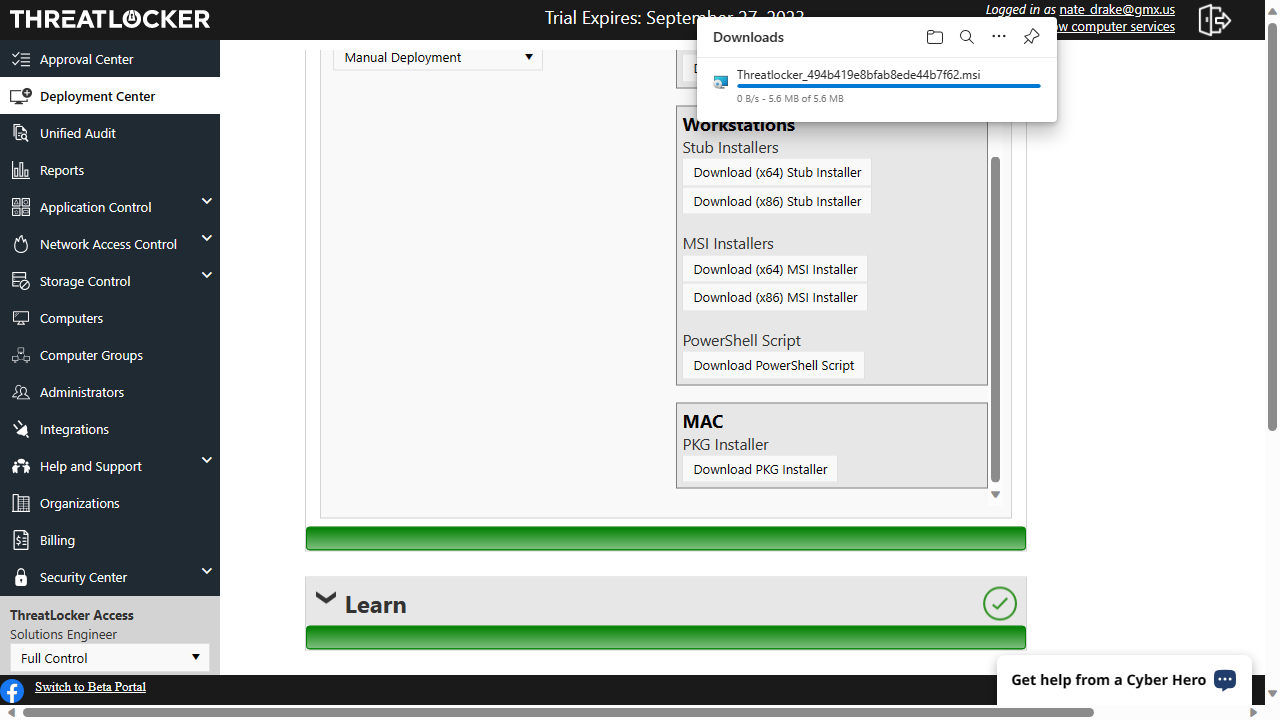
If you happen to go for a trial (as we did), you’ll be requested firm and make contact with particulars. After that, you’ll be able to log into the Threatlocker portal, and transfer over to the ‘Deployment Middle’ to put in the agent software program.
There are a number of methods of doing this, together with RMM (Remote Monitoring & Management), software program deployment device, Lively Listing and Energy Shell. We selected the guide set up utilizing the Home windows installer. There’s an MSI model however we opted as a substitute for the tiny ‘stub’ utility, which Threatlocker advises will set up the newest model of the ThreatLocker Agent.
Home windows (Servers and Workstations) and macOS are each supported. Sadly, we couldn’t discover Linux or cell gadgets talked about anyplace. Nevertheless, at press time, Threatlocker did have a job posting for a kernel software program developer with expertise in Linux, which may imply the platform is perhaps supported sooner or later.
Threatlocker: Interface
In distinction to Threatlocker’s options, the primary interface was considerably tough across the edges. At occasions, it felt extra like modifying a database, relatively than working in a web based portal.
Nonetheless, the left-hand pane was well-designed, with increasing sections. For instance, increasing ‘Utility Management’ lists selections reminiscent of ‘Insurance policies’, ‘Permitted Purposes’, ‘Purposes’ and ‘Tags’.
What we felt the platform actually lacked was a typical dashboard, a spot the place you’ll be able to see a fast heads-up of system standing, menace blocks, and so forth. A couple of pie charts and different infographics would have been useful, as effectively.
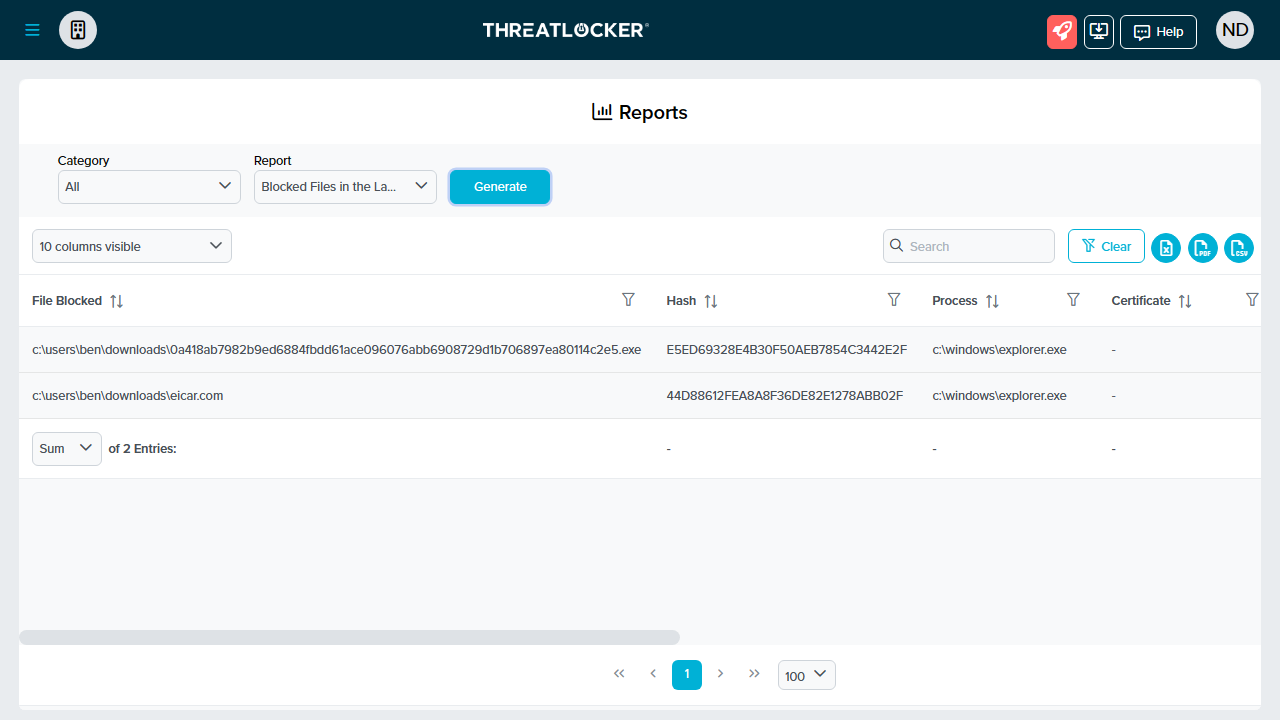
There’s a function to generate studies, the place you’ll be able to construct out any quantity of knowledge (for instance, blocked information within the final 24 hours), however these seem in a spreadsheet-like format. So, be ready for some clicking and dragging as a way to view all the knowledge.
That being stated, there’s something referred to as the “Beta” portal, which has a richer person interface (UI). You continue to gained’t get the basic dashboard, but it surely’s simpler to see and use all of the totally different choices. The left hand pane has additionally been changed with a dropdown menu.
We’re nonetheless ready for the Threatlocker Agent to get the ‘Beta therapy’ so that you’ll must dig via the spreadsheet type to see blocked information.
Threatlocker: Efficiency
Reviewing Threatlocker is one thing of an emotional curler coaster. The options had been thrilling, however the interface was considerably disappointing. The efficiency, but once more, acquired our hopes up. We check all of the platforms the identical approach: with a faux virus, an precise virus, after which we check out the logs.
Courtesy of EICAR, we tried to obtain a faux computer virus, via Microsoft Edge. On our first try, we couldn’t extract the file as a result of the permissions had been modified. Then we tried to obtain it uncompressed, however as soon as once more, Threatlocker Agent blocked it. This time, we additionally acquired a pop-up notifying us of the exercise. Curiously, the agent does embody a ‘Request Entry’ possibility, which can be helpful if an endpoint person desires to request permission to run a reputable program.
We then tried to obtain and run an precise virus and had been stopped in our tracks as soon as once more.
Lastly, we logged into the cloud console to test the logs. We used Threatlocker’s beta cloud console and noticed the total file names displayed, with none advantageous tuning by way of the mouse.
Threatlocker: Remaining verdict
We’ll take an unrefined interface with a robust platform, over a fancy-looking dashboard that crumbles below strain any day. Now we have to say – it’s relatively unfair that Threatlocker isn’t talked about in the identical sentence with heavy-hitters reminiscent of Malwarebytes, regardless of stellar efficiency.
It’s simple to register and set up. It has nice buyer assist. It really works effectively, and might simply be fine-tuned.
Whereas we do have a number of objections (no devoted firewall, lack of a graphically-rich agent, no assist for cell), they take away virtually nothing from the general impression.