Governments hacking enterprise
Just a few years in the past, zero-day assaults nearly solely focused finish customers. In 2021, GTIG noticed 95 zero-days, and 71 of them had been deployed towards person techniques like browsers and smartphones. In 2024, 33 of the 75 complete vulnerabilities had been geared toward enterprise applied sciences and safety techniques. At 44 % of the entire, that is the very best share of enterprise focus for zero-days but.
GTIG says that it detected zero-day assaults focusing on 18 completely different enterprise entities, together with Microsoft, Google, and Ivanti. That is barely decrease than the 22 corporations focused by zero-days in 2023, but it surely’s a giant improve in comparison with only a few years in the past, when seven corporations had been hit with zero-days in 2020.
The character of those assaults usually makes it laborious to hint them to the supply, however Google says it managed to attribute 34 of the 75 zero-day assaults. The most important single class with 10 detections was conventional state-sponsored espionage, which goals to collect intelligence with out a monetary motivation. China was the biggest single contributor right here. GTIG additionally recognized North Korea because the perpetrator in 5 zero-day assaults, however these campaigns additionally had a monetary motivation (normally stealing crypto).
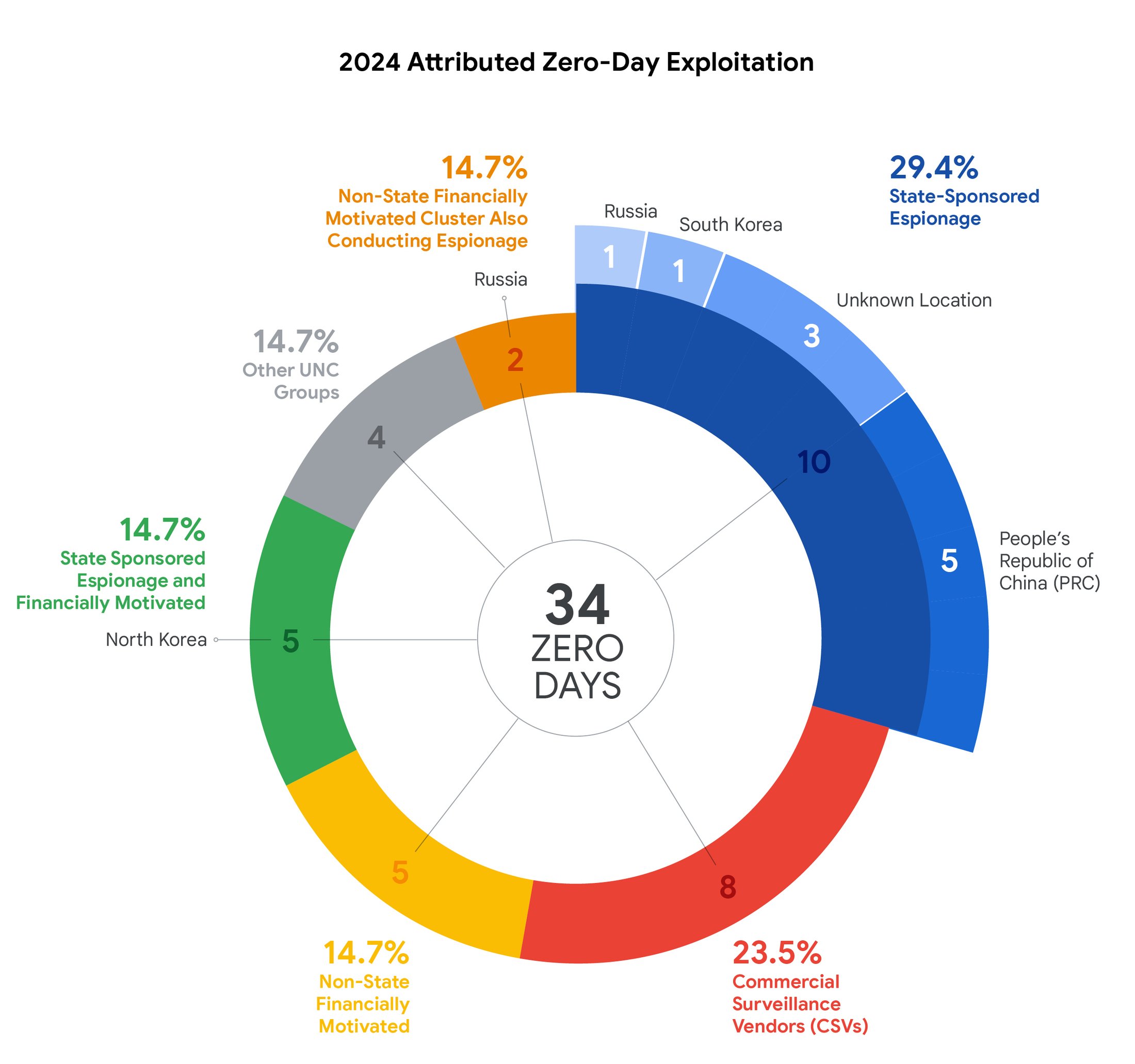
That is already a variety of government-organized hacking, however GTIG additionally notes that eight of the intense hacks it detected got here from industrial surveillance distributors (CSVs), corporations that create hacking instruments and declare to solely do enterprise with governments. So it is honest to incorporate these with different authorities hacks. This consists of corporations like NSO Group and Cellebrite, with the previous already topic to US sanctions from its work with adversarial nations.
In all, this provides as much as 23 of the 34 attributed assaults coming from governments. There have been additionally just a few assaults that did not technically originate from governments however nonetheless concerned espionage actions, suggesting a connection to state actors. Past that, Google noticed 5 non-government financially motivated zero-day campaigns that didn’t seem to interact in spying.
Google’s safety researchers say they anticipate zero-day assaults to proceed growing over time. These stealthy vulnerabilities will be costly to acquire or uncover, however the lag time earlier than anybody notices the risk can reward hackers with a wealth of data (or cash). Google recommends enterprises proceed scaling up efforts to detect and block malicious actions, whereas additionally designing techniques with redundancy and stricter limits on entry. As for the common person, properly, cross your fingers.

